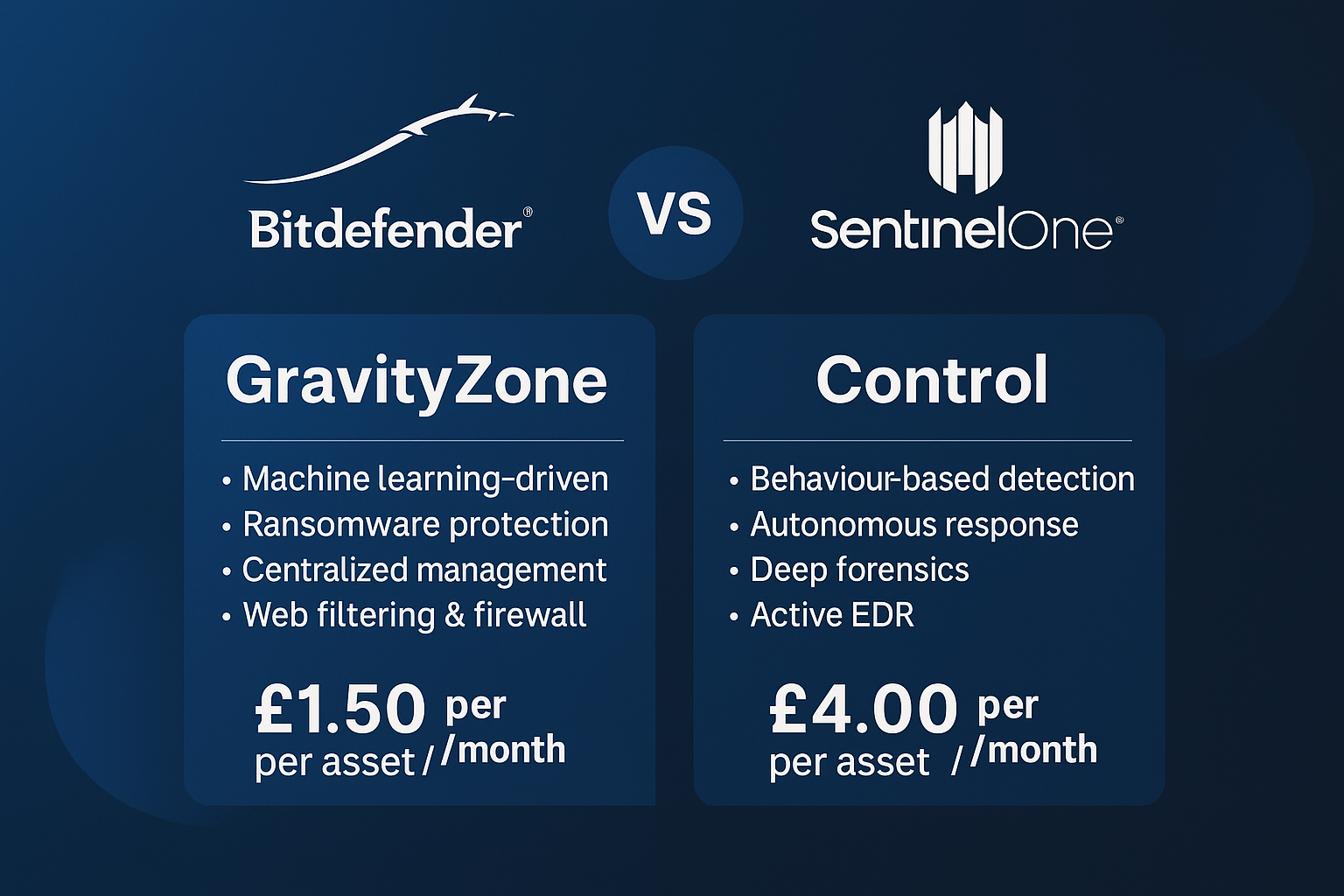
Bitdefender GravityZone is a comprehensive cybersecurity solution that protects endpoints, networks, and cloud services through advanced threat detection and prevention technologies. It integrates machine learning, heuristics, and behavior-based detection to combat malware, ransomware, phishing, and zero-day threats.
Key Features:
- Machine learning-driven malware detection
- Ransomware protection with anti-exploit technologies
- Centralized management console (cloud or on-premises)
- Web filtering, firewall, and device control
- Optional Patch Management and Full Disk Encryption modules
- Network attack defense and anti-phishing
- Lightweight agent with minimal system impact
Pricing: £1.50 per asset per month (excl. VAT). Annual subscription required.

SentinelOne Control is an advanced endpoint protection platform that leverages artificial intelligence to autonomously prevent, detect, and respond to threats in real-time. Unlike traditional antivirus, SentinelOne does not rely on signatures and is capable of handling both known and unknown threats without internet connectivity.
Key Features:
- AI-driven behavior-based threat detection
- Full autonomous response including ransomware rollback
- Complete endpoint visibility and deep forensics
- USB, Bluetooth, and firewall control policies
- Active EDR capabilities with attack storyline visualization
- Offline protection with no dependency on cloud lookups
- Cloud-native or on-premises management
Pricing: £4.00 per asset per month (excl. VAT). Annual subscription required.
Comparison & Conclusion
Comparison Table:

Conclusion:
Bitdefender GravityZone is a cost-effective, layered security solution well-suited for small to medium-sized businesses that require essential protection with optional add-ons.
SentinelOne Control offers high-end, autonomous security suitable for organizations needing robust ransomware protection, deep forensic insights, and full offline capabilities.
We recommend choosing based on your organization’s threat profile, IT resources, and desired level of automation.